
ISACA certifications are coveted in the information security and control industry. These credentials make it possible for employees to handle the most sensitive technical issues. They have passed rigorous testing and are certified by ISACA. They are given twice annually and contain more than 200 multiple-choice question that assess knowledge in four domains. Consequently, it is important to study hard and practice exams to prepare for the exam. You can also take ISACA certification classes to improve your chances of passing the exam.
If you're not sure whether you're ready to take ISACA, don't panic. You have many options for self-study online. Expert-led classes take just a few hours. If you'd rather learn in-person, ISACA offers in-person training. ISACA's online instructor-led courses are especially popular. But, if your schedule is limited, you can take a selfpaced course.

CRISC certification is the most recent ISACA designation. It covers information systems risks and includes risk monitoring, response, risk identification, risk management controls, and risk monitoring. CRISC does not offer year-round exams, however ISACA offers CISA and CISM revision courses. For information on these training courses, contact EGIT. ISACA has approved all CISA and CISM revision courses.
CISA exams are the most time-consuming and challenging of all ISACA certifications. This certification requires five years of full-time work experience in the field of information security. Applicants must be eligible for the CISA exam within five months of clearing the exam, and they must have been an IS manager for at least three years. Candidates will be provided with various materials and the exam costs $50. CISA exams can either be taken by the CRISC or CGEIT.
IT governance plays an essential role in monitoring and controlling IT resources. It includes processes that maximize the efficiency of IT infrastructure, and provide business insight. IT governance covers strategic management, risk control, and optimizing IT resources. ISACA certifications are granted to individuals and businesses working in the IT industry. These ISACA certifications give you a taste of what ISACA certifications are like. It is possible to be surprised at all the benefits that it provides.
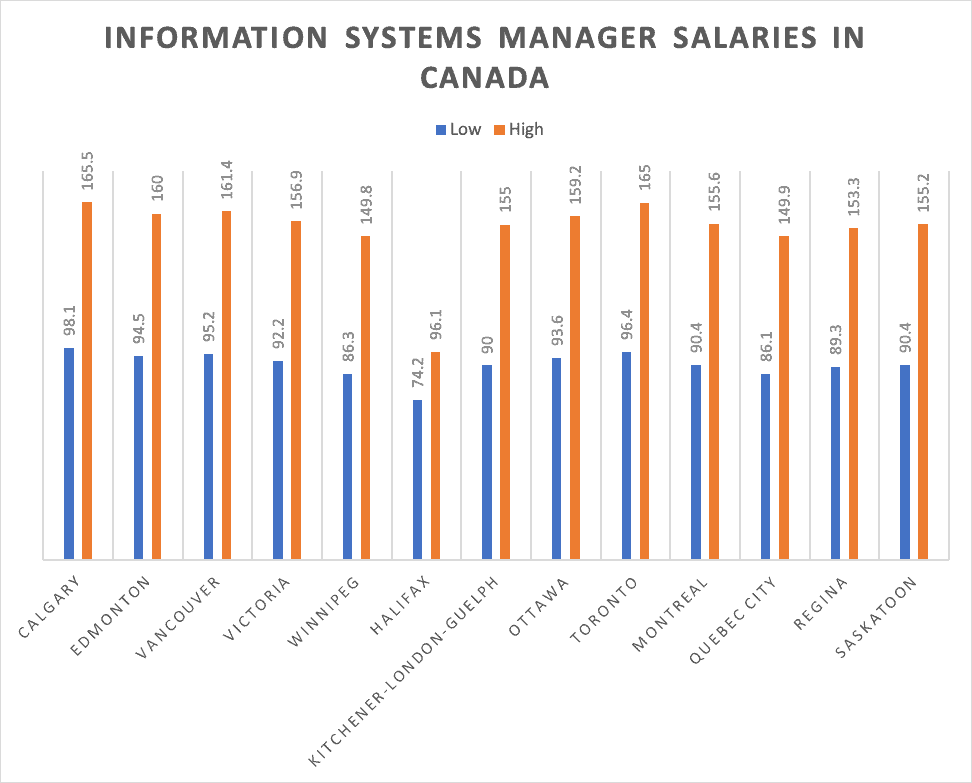
Certified Information Security Auditor (CISA), is for IT professionals. This certification, which is the highest-paid in ISACA, requires that successful candidates demonstrate their abilities in managing, monitoring and designing enterprise information safety. You must also have at least five years experience in information safety. It requires at least five years of field experience, as well three years experience as security manager. This is the perfect certification for those interested in managing or designing enterprise information security.
CPE credit is available for CISA designation holders who participate in ISACA activities. Serving on boards, committees, serving as a chapter officers, and taking part in other activities of ISACA is all possible. CPE hours are earned for every hour of participation. They can be used towards more than one ISACA certification. If you are looking to earn CPE credits through ISACA courses, you will be able to get 20 hours each year.
FAQ
Does cybersecurity require a lot math?
It's an integral part our business and we know that it won't go away soon. We must keep up with technology and ensure we do everything we can to defend ourselves against cyber-attacks.
That means finding ways to make sure that the systems we use every single day are secure without worrying too much about the technical details.
This must be done while keeping costs under control. These issues are constantly being improved upon.
But if we get it wrong, then we can lose out on opportunities, miss out on revenue, hurt our customers and even put lives at risk. We must ensure that we use our time wisely.
When there are many other areas to focus on, it is important not to go over every aspect of cybersecurity.
Therefore, we have a dedicated group that is focused on this issue. They are called "cybersecurity specialists" because they know exactly what to do and how to make those changes happen.
How do I study for cyber security certification?
The certifications in cyber security are essential for anyone working in the IT industry. The most common courses available include CompTIA Security+ (1), Microsoft Certified Solutions Associate - Security (2), and Cisco CCNA Security Certification (3). These are all recognized by employers and provide an excellent foundation on which to build. You have many other options: Oracle Certified Professional - Java SE 7 Programmer (4), IBM Information Systems Security Foundation (5), SANS GIAC (6).
You have the freedom to choose, but be sure to know what you are doing.
How do I prepare for my certification exams?
There are many options for how to prepare. It is possible to go through the entire syllabus and study it thoroughly before you sit the exam. The exam guidebook can be read in its entirety before sitting for the exam. For a quick test of your understanding, you might also be able to attempt some questions. A local community college could be a good option. There you will have the opportunity to meet other students who have passed the certification exam.
Many websites offer free exam preparation materials. However, you can only purchase one electronic copy of the exam manual. This copy should be saved safely. A CD/DVD drive is a good choice.
Some companies even offer self-study guides. These usually cost between $100 and $400. These include flashcards and quizzes, as well as other features. Many of these products also allow you online exams.
What are the future trends for cybersecurity?
The security industry continues to evolve at an extraordinary rate. Technology is changing rapidly. Older technologies are updated and new ones are becoming obsolete. The threats we face change all the time. Our experts can provide you with a comprehensive overview of the current situation or delve into the most recent developments.
This site has everything you could need
-
Latest news on attacks and vulnerabilities
-
Here are some best practices to deal with the latest threats
-
This guide will help you stay ahead of the curve
The future holds many opportunities. It is impossible to know what lies ahead. We can only plan for the future and hope to be lucky.
The headlines are all you need to know about the future if you really want information. They tell us that the greatest threat isn't currently coming from hackers or viruses. Instead, it's governments.
Governments around the world are continuously trying to spy on their citizens. They use advanced technology, such as AI, to monitor people's online activities and track their movements. To build detailed profiles of individuals or groups, they collect data from everyone they meet. Privacy to them is an obstacle to national security.
This power has been used by governments to target individuals. Experts think that the National Security Agency might have already used its powers for influence in Germany and France's elections. Although we don't know if the NSA targeted these countries intentionally or not, it makes sense when you consider it. You must make sure they don't stand between you and your goal to control the people.
This isn’t a hypothetical scenario. History shows us that dictatorships have been known to target their opponents by hacking their phones and stealing their data. There seems to be no limit to the extent that governments can do to maintain control over their subjects.
Although you may not be concerned about government surveillance, corporate spying might still concern you. There is no evidence that large corporations may track your online movements. Facebook, for example, tracks your browsing history without asking permission. Google claims it doesn’t sell your data, but there isn’t any proof.
In addition to being concerned about what happens when governments are involved, you also need to consider how to protect yourself when it comes to corporations. It is a good idea to learn about cybersecurity if you are going to work in IT. You could prevent companies accessing sensitive information. It is possible to teach your employees how you can spot potential phishing schemes, and other forms social engineering.
Cybercrime is, in short, one of the most pressing problems facing our society today. Governments, hackers, criminals, and terrorists constantly work together to steal your personal data and damage your computer systems. There are solutions for every problem. All you have to do is to find the right place to start.
Which IT certification is the most lucrative?
There doesn't appear to be an answer. It seems that Microsoft certifications attract more money.
What are the best IT courses?
Passion is essential for success in the technology field. Passion is key to success in the technology field. If you are not passionate about your work, don't worry. This industry requires hard work and dedication. You must also be able to adapt quickly to changes and learn quickly. Schools must prepare students to adapt to such changes. They must help students think critically and use their creativity. These skills will help them when they join the workforce.
Experience is second in technology learning. Most people who want to pursue a career in tech start doing it right after graduation. This field requires years of practice to master. Internships, volunteering, part time jobs, and so on are all ways to gain experience.
Practical training is the best. It's the best and most effective way to learn. If you are unable to find a volunteer or full-time job, consider taking classes at community colleges. Many universities offer classes for free through their Continuing Education programs.
Statistics
- The median annual salary of computer and information technology jobs in the US is $88,240, well above the national average of $39,810 (bls.gov).
- The number of IT certifications available on the job market is growing rapidly. According to an analysis conducted by CertifyIT, there were more than 2,000 different IT certifications available in 2017,
- The global IoT market is expected to reach a value of USD 1,386.06 billion by 2026 from USD 761.4 billion in 2020 at a CAGR of 10.53% during the period 2021-2026 (globenewswire.com).
- The top five countries contributing to the growth of the global IT industry are China, India, Japan, South Korea, and Germany (comptia.com).
- Employment in computer and information technology occupations is projected to grow 11% from 2019 to 2029, much faster than the average for all occupations. These occupations are projected to add about 531,200 new jobs, with companies looking to fill their ranks with specialists in cloud computing, collating and management of business information, and cybersecurity (bls.gov).
- The global information technology industry was valued at $4.8 trillion in 2020 and is expected to reach $5.2 trillion in 2021 (comptia.org).
External Links
How To
How can I begin to learn about cyber security
People who have been involved in computer technology for many years are often familiar with the term hacking. This may be confusing for some.
Hacking is a technique that allows unauthorized access of computers, networks, or any other system. It uses techniques like viruses, trojans. spyware.
Cybersecurity is now an industry. It offers methods to protect against these attacks.
It is important to understand how hackers work to help you stay safe online. We have compiled this information to help you get started on your journey towards becoming more knowledgeable about cybercrime.
What Is Cyber Security?
Cyber security refers to protecting computers against external threats. Hacking your system can give someone access to your files, money or other information.
There are two types in cybersecurity: Computer Forensics, and Computer Incident Response Teams.
Computer forensics is the study of a computer's behavior after a cyberattack. It's done by experts who search for evidence that will lead them to the attacker responsible. Computers are analyzed to detect signs of hacking or damage from malware or viruses.
CIRT is the second form of cybersecurity. Computer incidents can be handled together by CIRT groups. They use their knowledge to stop attackers and prevent them from causing serious harm.